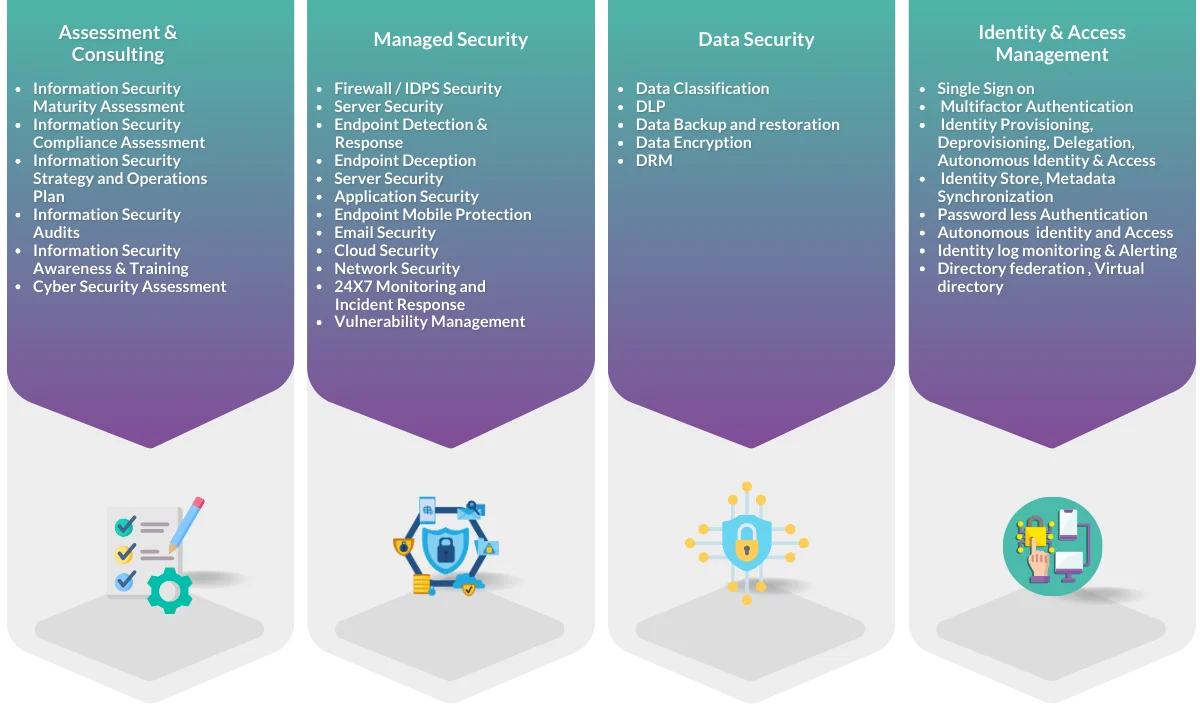
- Assessment and Consulting
- Managed Security Services
- Identity and Access Management Services
- Data Security
Security
The cyber threat landscape has rapidly evolved over the past few years, due to which cybersecurity has now become a high-priority business risk. i-Source designs, installs, and integrates perimeter, network, and endpoint solutions with advanced threat protection so you can reduce risks and know you’re safe and compliant. Depending on your specific cybersecurity requirements, we secure your applications, cloud & hybrid infrastructure as well as endpoints from anticipated threats.
Our Security Stack
i-Source develops and implements effective information security strategies to protect sensitive data, intellectual property and confidential information from unauthorized access and reduce risk of security incidents. i-Source Security Services protect the enterprise assets across endpoints, networks, applications, and cloud infrastructure against Zero-day attacks, Viruses, Malwares, and Data leakages.
We cover following aspects of enterprise security:
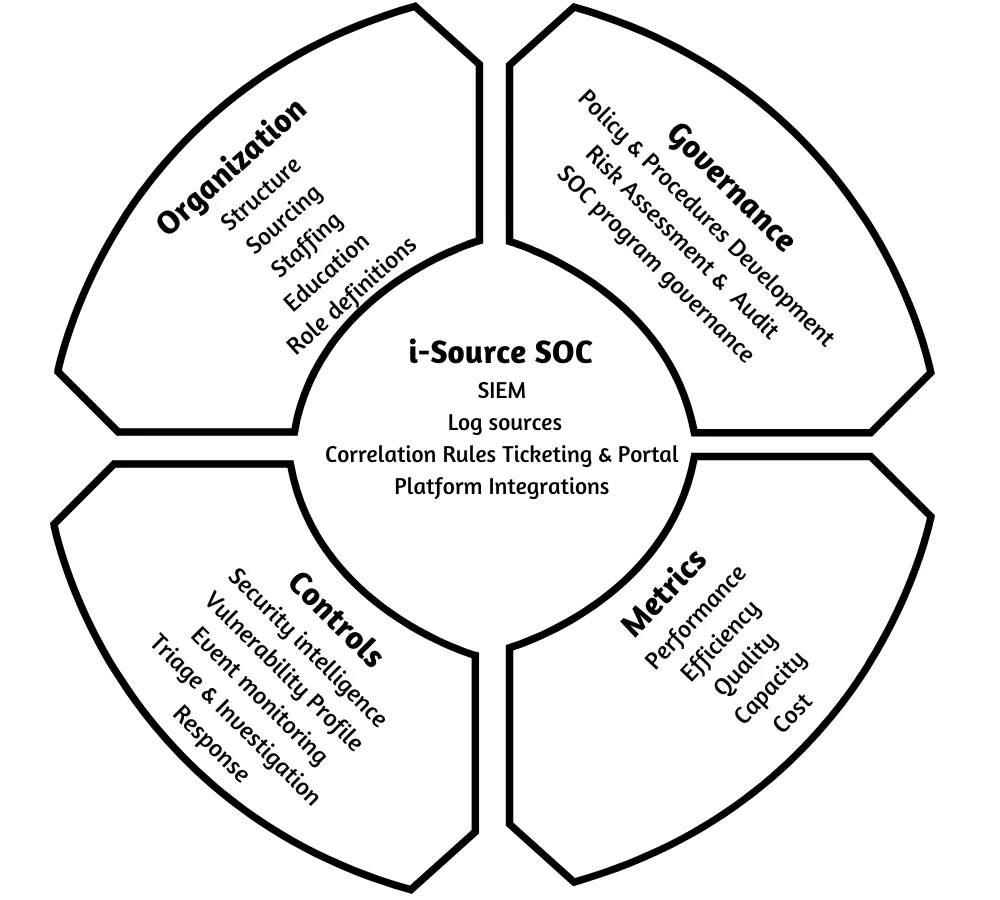
Our Holistic Approach to Security Operations Management
i-Source designs, builds, and operates Security Operations Centers. The dedicated/managed SOC service provides 24×7 technical support and security monitoring support across the enterprise. To ensure fully operational and fault-free managed services, we follow a well-defined SOC monitoring process, metrics driven organization hierarchy, and availability of security experts.
- Comprehensively assess and manage information security risks
- Achieve NIST compliance, prevent cyber-attacks, minimize risk of data breaches
- Protect sensitive data from cyberattack, ensure compliance with regulations & standards
- Ensure Business Continuity, protect business reputation